04. Understanding Attack Methods
Understanding Attack Methods
ND545 C3 L2 A04 Understanding Attack Methods Part 1 V3
Overview
While there are many different threats, threat actors, and scenarios, they typically follow a similar process. These have been summarized in the common cyber attack kill chain, and attack frameworks like MITRE ATT&CK.
Cyber Attack Process
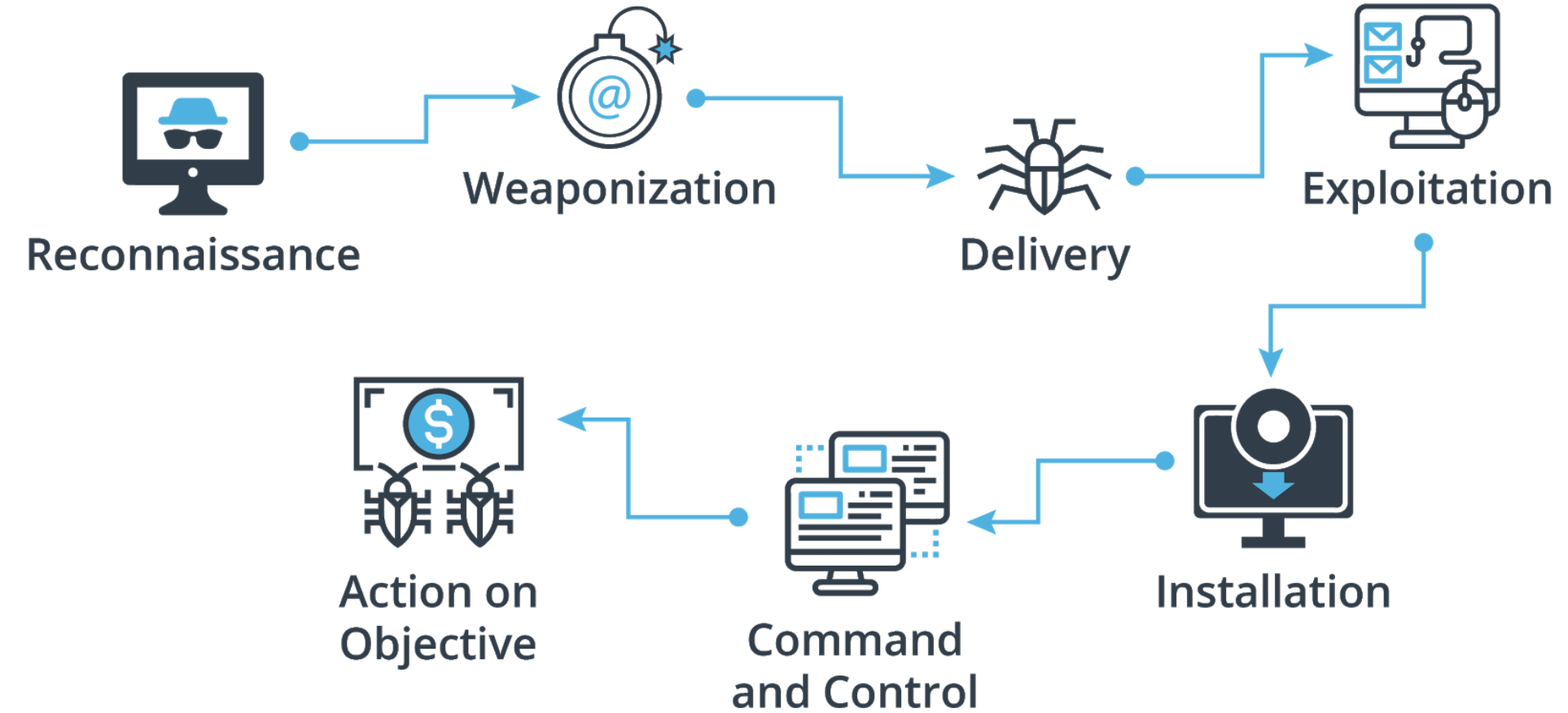
There are 7 common steps in the Cyber Attack Process, first articulated by Lockheed Martin as the cyber attack kill chain:
- Reconnaissance: The threat actor conducts research to find as much information as possible on the targets they want to attack, including vulnerabilities and weaknesses.
- Weaponization: The threat actor creates or acquires the arsenal for attack, such as malware.
- Delivery: The weapon is launched against the target and the operation begins.
- Exploitation: The threat actor must take advantage of vulnerability to gain access.
- Installation: The threat actor might install a backdoor or create ways to keep their access for the attack.
- Command and control: The threat actor enables remote control and manipulation of the target.
- Action on objectives: The threat actor accomplishes their mission and completes the attack goal.
Reference:
First articulated by Lockheed Martin as the “kill chain” now used across the industry as a standard (https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html)
The MITRE ATT&CK Framework
ND545 C3 L2 A04 Understanding Attack Methods Part 2
ATT&CK refers to Adversarial Tactics, Techniques, and Common Knowledge. MITRE's attack framework is created to document common tactics, techniques, and procedures threats use against various enterprise systems. It outlines how attackers exploit vulnerabilities and weaknesses in systems to carry out attacks. As you work to find and fix vulnerabilities, this is a great resource to reference.
Take a moment to explore the framework here: https://attack.mitre.org